Keyfactor Command is an n-tier application, consisting of a web/presentation layer, application tier, and database tier. In addition, Keyfactor Command optionally includes a number of enrollment![]() Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). and management components to help facilitate secure and/or automated certificate issuance and delivery to various server and client platforms. The following sections provide views of the Keyfactor Command architecture from a logical and physical standpoint.
Certificate enrollment refers to the process by which a user requests a digital certificate. The user must submit the request to a certificate authority (CA). and management components to help facilitate secure and/or automated certificate issuance and delivery to various server and client platforms. The following sections provide views of the Keyfactor Command architecture from a logical and physical standpoint.
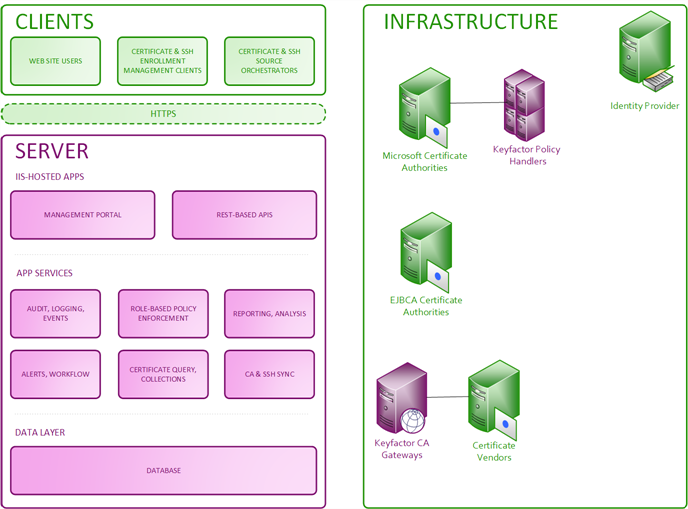
Figure 445: Keyfactor Command Logical Architecture Diagram
The Keyfactor Command solution includes the following logical components:
- Client / Orchestrator
 Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. Tier:
Keyfactor orchestrators perform a variety of functions, including managing certificate stores and SSH key stores. Tier:- Certificate Enrollment and Management Tools—While many certificate management functions can be performed in a completely agentless fashion, Keyfactor Command provides a number of enrollment and management tools to enable enhanced functionality where needed.
- Certificate Source Orchestrators (aka Agents) and Gateways—Keyfactor Command gathers information about an enterprise’s certificates and SSH
 The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. keys from a number of different sources, including Microsoft and EJBCA CA
The SSH (secure shell) protocol provides for secure connections between computers. It provides several options for authentication, including public key, and protects the communications with strong encryption. keys from a number of different sources, including Microsoft and EJBCA CA A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. databases, SSL
A certificate authority (CA) is an entity that issues digital certificates. Within Keyfactor Command, a CA may be a Microsoft CA or a Keyfactor gateway to a cloud-based or remote CA. databases, SSL TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. scans, SSH key scans, API
TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are protocols for establishing authenticated and encrypted links between networked computers. scans, SSH key scans, API A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command.-based import, Java keystores, PEM
A set of functions to allow creation of applications. Keyfactor offers the Keyfactor API, which allows third-party software to integrate with the advanced certificate enrollment and management features of Keyfactor Command.-based import, Java keystores, PEM A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. certificate stores, F5 devices, NetScaler devices, Amazon Web Services (AWS) locations, select certificate vendor certificates via gateways, and manual import through the Keyfactor Command Management Portal.
A PEM format certificate file is a base64-encoded certificate. Since it's presented in ASCII, you can open it in any text editor. PEM certificates always begin and end with entries like ---- BEGIN CERTIFICATE---- and ----END CERTIFICATE----. PEM certificates can contain a single certificate or a full certifiate chain and may contain a private key. Usually, extensions of .cer and .crt are certificate files with no private key, .key is a separate private key file, and .pem is both a certificate and private key. certificate stores, F5 devices, NetScaler devices, Amazon Web Services (AWS) locations, select certificate vendor certificates via gateways, and manual import through the Keyfactor Command Management Portal.
- Web Tier:
- Management Portal—Keyfactor Command includes a web-based Management Portal that provides a PKI
 A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. operations dashboard for administrators. It also enables certificate officers to easily search for and locate certificates and then perform management functions on them such as revocation or recovery. In addition, Keyfactor Command allows every certificate to be tagged with additional customer-defined metadata
A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. operations dashboard for administrators. It also enables certificate officers to easily search for and locate certificates and then perform management functions on them such as revocation or recovery. In addition, Keyfactor Command allows every certificate to be tagged with additional customer-defined metadata Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. about the certificate, such as points of contact, certificate/app owners, etc. From within the Management Portal, administrators can inventory and manage secure shell (SSH) keys across the enterprise, while users can issue new SSH keys.
Metadata provides information about a piece of data. It is used to summarize basic information about data, which can make working with the data easier. In the context of Keyfactor Command, the certificate metadata feature allows you to create custom metadata fields that allow you to tag certificates with tracking information about certificates. about the certificate, such as points of contact, certificate/app owners, etc. From within the Management Portal, administrators can inventory and manage secure shell (SSH) keys across the enterprise, while users can issue new SSH keys. - Enrollment Web Pages—Keyfactor Command includes issuance capabilities to a wide array of platforms, including Mac auto-enrollment, PKCS#12
 A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers.-based certificate issuance, and web-based CSR
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers.-based certificate issuance, and web-based CSR A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. submission for administrator enrollment. PKCS#12 (PFX
A CSR or certificate signing request is a block of encoded text that is submitted to a CA when enrolling for a certificate. When you generate a CSR within Keyfactor Command, the matching private key for it is stored in Keyfactor Command in encrypted format and will be married with the certificate once returned from the CA. submission for administrator enrollment. PKCS#12 (PFX A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers.) and CSR enrollment are supported against Microsoft CAs in the local forest
A PFX file (personal information exchange format), also known as a PKCS#12 archive, is a single, password-protected certificate archive that contains both the public and matching private key and, optionally, the certificate chain. It is a common format for Windows servers.) and CSR enrollment are supported against Microsoft CAs in the local forest An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers., remote CAs—with or without trust relationships—and non-domain-joined Microsoft and EJBCA CAs.
An Active Directory forest (AD forest) is the top most logical container in an Active Directory configuration that contains domains, and objects such as users and computers., remote CAs—with or without trust relationships—and non-domain-joined Microsoft and EJBCA CAs. - Web APIs—Keyfactor Command is implemented with a robust and continually growing set of APIs that allow integration of Keyfactor Command functionality with the set of Keyfactor Command clients and orchestrators, as well as third-party or customer-created software or scripts.
- Management Portal—Keyfactor Command includes a web-based Management Portal that provides a PKI
- App Tier:
- Event History and Audit Logging—Keyfactor Command maintains a record of operations that are performed on a certificate and the individual who performed the operation. This includes information such as initial synchronization date, additions to and removals from certificate stores, certificate recovery, and certificate revocation.
- Role-Based Policy Enforcement—Keyfactor Command offers a rich, role-based permissions model that allows you to create your own roles as needed within the Keyfactor Command Management Portal. Users can be assigned to roles based upon Active Directory group memberships or individually, and then each role can be assigned granular Keyfactor Command permissions such as report creation, certificate revocation or renewal, or metadata update.
- Dashboard and Report Engine—Keyfactor Command contains a dynamic dashboard along with several built-in reports generated using the Logi Analytics Platform.
- Certificate Query & Collections—Keyfactor Command allows certificate administrators to query the certificate database using various search criteria. In addition, the bulk of Keyfactor Command’s reporting and automated notification functionality can be driven through certificate collections, which are a user-definable mechanism that allows organizations to report on groups of certificates based on selection criteria.
- Workflow
 A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked. Builder—The workflow builder in Keyfactor Command allows you to easily automate event-driven tasks when a certificate is requested or revoked. The workflows can be configured with multiple steps between the start and end of the operation that offer a simple way to configure notifications, approvals, and end-to-end automation. This provides for operational agility in an intuitive and easy-to-configure manner. The workflow builder is highly customizable with options to execute PowerShell scripts, invoke REST requests, send email messages, and require one or more approvals built in, and facilities to build custom steps to allow many more functions to be built as needed.
A workflow is a series of steps necessary to complete a process. In the context of Keyfactor Command, it refers to the workflow builder, which allows you automate event-driven tasks when a certificate is requested or revoked. Builder—The workflow builder in Keyfactor Command allows you to easily automate event-driven tasks when a certificate is requested or revoked. The workflows can be configured with multiple steps between the start and end of the operation that offer a simple way to configure notifications, approvals, and end-to-end automation. This provides for operational agility in an intuitive and easy-to-configure manner. The workflow builder is highly customizable with options to execute PowerShell scripts, invoke REST requests, send email messages, and require one or more approvals built in, and facilities to build custom steps to allow many more functions to be built as needed. - Alert Notice Generator—Keyfactor Command allows you to configure customized email notifications for impending certificate expiration, revocation expiration, pending certificate requests, issued certificate requests and denied certificate requests. These notifications can be sent at configurable intervals, and may contain ASCII or HTML content, along with relevant information about the certificate or request in question (e.g. subject DN
 A distinguished name (DN) is the name that uniquely identifies an object in a directory. In the context of Keyfactor Command, this directory is generally Active Directory. A DN is made up of attribute=value pairs, separated by commas. Any of the attributes defined in the directory schema can be used to make up a DN., issuer, thumbprint, template
A distinguished name (DN) is the name that uniquely identifies an object in a directory. In the context of Keyfactor Command, this directory is generally Active Directory. A DN is made up of attribute=value pairs, separated by commas. Any of the attributes defined in the directory schema can be used to make up a DN., issuer, thumbprint, template A certificate template defines the policies and rules that a CA uses when a request for a certificate is received., custom metadata, etc.)
A certificate template defines the policies and rules that a CA uses when a request for a certificate is received., custom metadata, etc.) - Certificate Request Alerting—Keyfactor Command provides interfaces through which administrators can request certificates that require CA-level manager approval, interfaces where the approvers can either issue or deny the certificate request, and interfaces where the requesters can then download the certificates. This, along with the notice generator, provides an end-to-end flow for certificate requests that require CA-level manager approval.
- Alert Handlers—In addition to the notice generator that provides email alerts for SSH key and certificate expiration and enrollment workflow, Keyfactor Command also provides optional handlers that can be used in the certificate request and expiration alerts to output the information to the event log rather than sending it via email, run a PowerShell script, or automatically renew expiring certificates that are found in certificate store locations.
- Keyfactor Command Service—The Keyfactor Command Service (a.k.a. the timer service) is designed to continually keep the Keyfactor Command SQL database synchronized with the contents of every configured Microsoft and EJBCA CA database in the organization as well as external certificates located on servers it can scan. The service can perform full or partial scans of different CAs at user-defined intervals. This enables a rapidly-accessible, easily queried mirror of CA database information that can then be put to use via Keyfactor Command. Synchronization of CA information is supported for Microsoft CAs joined to the local forest, remote domain-joined Microsoft CAs—with or without trust relationships—and non-domain-joined Microsoft and EJBCA CAs. The Keyfactor Command Service is also responsible for executing a variety of periodic tasks, including scheduled reports, alerts and cleanup jobs.
- Data Tier:
- SQL Database—Keyfactor leverages a Microsoft SQL Server database to store the information that Keyfactor Command uses.
- Microsoft Certification Authority Components:
- RFC 2818 Policy Handler—The RFC 2818 Policy Handler integrates with the Microsoft CA to allow you to automate the addition of a DNS
 The Domain Name System is a service that translates names into IP addresses. SAN
The Domain Name System is a service that translates names into IP addresses. SAN The subject alternative name (SAN) is an extension to the X.509 specification that allows you to specify additional values when enrolling for a digital certificate. A variety of SAN formats are supported, with DNS name being the most common. matching the CN
The subject alternative name (SAN) is an extension to the X.509 specification that allows you to specify additional values when enrolling for a digital certificate. A variety of SAN formats are supported, with DNS name being the most common. matching the CN A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). of the requested certificate for selected templates.
A common name (CN) is the component of a distinguished name (DN) that represents the primary name of the object. The value varies depending on the type of object. For a user object, this would be the user's name (e.g. CN=John Smith). For SSL certificates, the CN is typically the fully qualified domain name (FQDN) of the host where the SSL certificate will reside (e.g. servername.keyexample.com or www.keyexample.com). of the requested certificate for selected templates. SAN Attribute Policy Handler—The SAN Attribute Policy Handler allows the addition of SANs not included in the CSR when making a CSR enrollment request. The added SANs will overwrite any existing SANs in the CSR. This functionality is the same as that seen with the Microsoft default policy module for the CA as a whole when the CA EDITF_ATTRIBUTESUBJECTALTNAME2 flag is set except the SAN Attribute Policy Handler provides the ability to control SAN addition on a template-by-template basis without the need to enable the Microsoft CA EDITF_ATTRIBUTESUBJECTALTNAME2 flag.
- Whitelist Policy Handler—The Whitelist Policy Handler integrates with the Microsoft CA to allow you to restrict certificate enrollment on that CA for a configured certificate template or templates to only designated client machines. This allows you, for example, to force certificate enrollment for web server certificates to be accepted only via the Keyfactor Command Management Portal and denied when coming from the Microsoft certificates MMC or IIS on the target servers for web server certificates.
- RFC 2818 Policy Handler—The RFC 2818 Policy Handler integrates with the Microsoft CA to allow you to automate the addition of a DNS
- Enterprise Infrastructure:
- Certification Authorities—Keyfactor Command has been built from the ground up to make it easier to operate organizational PKIs. This allows you to benefit from Keyfactor Command’s extended features around Microsoft CA capabilities such as certificate templates, enrollment and recovery agents, and private key
 Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. recovery. Keyfactor Command's integration with EJBCA provides support for capabilities such as certificate profiles, end entity profiles, enrollment, and revocation.
Private keys are used in cryptography (symmetric and asymmetric) to encrypt or sign content. In asymmetric cryptography, they are used together in a key pair with a public key. The private or secret key is retained by the key's creator, making it highly secure. recovery. Keyfactor Command's integration with EJBCA provides support for capabilities such as certificate profiles, end entity profiles, enrollment, and revocation. - Identity Providers—Keyfactor Command relies on an identity provider to support authentication to the Management Portal and the Keyfactor API and supporting group memberships for Keyfactor Command role assignments. Historically, the product has been integrated with Microsoft Active Directory, using AD for Microsoft CA and certificate template enumeration and for the inclusion of AD account attributes in the content of issued certificates. With the release of Keyfactor Command version 11.0, support for identity providers expands beyond Active Directory. Users may choose between Active Directory and an open authorization (OAuth) 2.0 compliant identity provider with a complete implementation of the OpenID Connect (OIDC) protocol including the Keyfactor-provided Keyfactor Identity Provider.
- Certification Authorities—Keyfactor Command has been built from the ground up to make it easier to operate organizational PKIs. This allows you to benefit from Keyfactor Command’s extended features around Microsoft CA capabilities such as certificate templates, enrollment and recovery agents, and private key